Don't Take The Bait.
The Do's and Don't of Cyber Security
Cyber Security… we’ve all heard this term used a million times.
Just read the news and you’ll see another major company whose security was
breached. We, the consumers, are left feeling hopeless that our private
information has fell in to the hands of a faceless villain who is quick to sell
our priceless information on the dark net. We’ve heard of family and friends
whose computer has been encrypted or infected with a virus. This next level of
viruses are very destructive and are known as Ransomware.
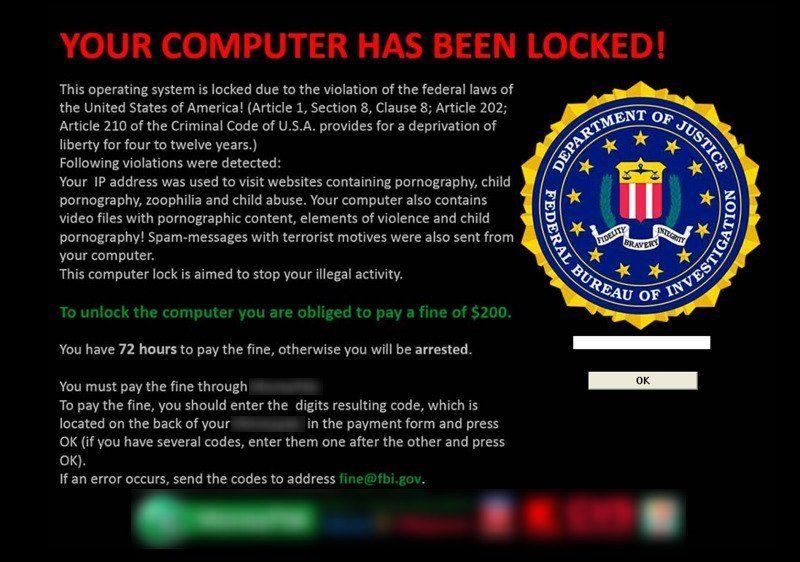
Once executed on your computer, ransomware can either lock the computer screen, or, in the case of crypto-ransomware, encrypt your files. In the first scenario, a full-screen image or notification is displayed on the infected system's screen sometimes claiming to be from the FBI, IRS or some other authority, preventing victims from using their system. It commonly shows instructions on how users can pay for the ransom. The good news is that most of the time, these files can be recovered without having to pay the ransom.
The second type of ransomware, crypto-ransomware is much more destructive. It prevents access to your files by encrypting them and holding them for ransom. Yes, we said RANSOM! Without the encryption “key”, there is no way to unlock your files. Ransoms can be anywhere from a few hundred dollars to thousands of dollars, usually asked for in bitcoin or gift cards. If you thought it couldn’t get worse, it does… there is no guarantee they will send you the “key” after paying their ransom. You can’t exactly trust these criminals.
Most computers get infected by clicking malicious links via email, opening infected attachments or visiting compromised websites.
What can you do to protect yourself?
- Always be cautious. We’re
New Yorkers, we are cautious of everything. Embrace the NYC way when it comes
to cyber security.
- Most viruses happen when
people search for a specific topic and misspell it. The most commonly searched
words are the most dangerous misspellings.
- Below is an example of a bait
email our CTO, Sherif Mikhail, received. At first look, it looks pretty official. Your first instinct may be to click the link. However, it should be determined if
the email is legit. This email was pretty easy to spot as a fake, just
by looking at the sender’s email address. Take a look below, not so official. Always check the senders email address before
clicking any link or downloading any files. While this is not a sure way to
determine its legitimacy, it’s a start. If you are still unsure, call the company
directly or go to the company’s website to check to see if they’ve recently sent
emails asking for that information.
Since no one, not even the best Tech Gods are fully protected, you must be prepared. Having a backup of all your files and photos is extremely important. External hard drives were a common back up solution, but today’s viruses are far too advanced and can infect those drives as well.
For a secure backup, we recommend a cloud provider that archives previous copies of your files, most of these will back up your files automatically daily or a few times a day, depending on how you set up your backup. Many also offer an email report of your backup jobs so you know your files are being safely protected. A provider such as Google Drive, only keeps current files, thus resulting in the possible upload of your infected files. There goes the back up! Your photos and files are priceless, so it’s best to invest few dollars and pay for a backup solution that offers an archive of your files.
Now that you’re in the know, be prepared. Our techs can help with a backup plan, so you don’t find yourself a victim.
Remember… Don’t Take The Bait!